Information Technology (IT) is essential for the growth and development of businesses. Enterprises and organisations are spending significant portion of their budget for rolling out their IT roadmap and deploy number of IT enabled services that are essential for the survival and growth of business. These deployed resources are prone to vulnerabilites that can be exploited by hacker groups and are thus risky. This risk in cybersecurity can further cause risk to the business.
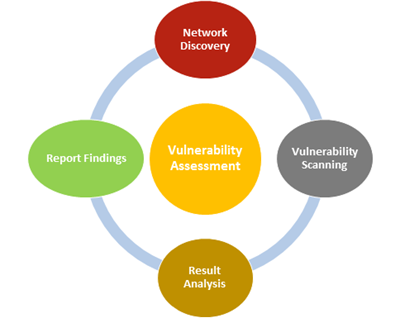
A vulnerability analysis is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system.
Vulnerability Analysis provides enterprises with a more comprehensive application evaluation than any single test alone. The Vulnerability Assessment approach gives an organisation a more detailed view of the threats facing its applications, security flaws, overall risks and assests enabling the business to better protect its systems and data from malicious attacks.